MobileAudit – SAST and Malware Analysis for Android Mobile APKs
Django Web application for performing Static Analysis and detecting malware in Android APKs
Components

- db: PostgreSQL 13
- nginx: Nginx 1.18.0
- web: Mobile Audit App
Docker Base images
Image is based on python buster. Link to Docker Hub image
| Image | Tags | Base |
|---|---|---|
| mpast/mobile_audit | 1.2.0 | python:3.9.1-buster |
| mpast/mobile_audit | 1.1.0 | python:3.9.0-buster |
| mpast/mobile_audit | 1.0.0 | python:3.9.0-buster |
Main features
- Uses Docker for easy deployment in multiplatform environment
- Extract all information of the APK
- Analyze all the source code searching for weaknesses
- All findings are categorized and follows CWE standards
- Also highlight the Best Practices in Secure Android Implementation in the APK
- The findings can be edited and the false positives can be triaged and deleted
- All scan results can be exported to PDF
- User authentication and user management
- API v1 with Swagger and ReDoc
- TLS
Export to MarkdownExport to CSVLDAP integrationDynamic page reload
Integrations
Virus Total (API v3)
It checks if there has been an scan of the APK and extract all its information. Also, there is the possibility of uploading the APK is selected a property in the environment (Disabled by default).
It is possible to upload the findings to the defect manager.
It checks in the database if there are URLs in the APK that are related with Malware.
Installation
Using Docker-compose:
The provided docker-compose.yml file allows you to run the app locally in development. To start the container, run:
docker-compose up
If there are changes to the local Application Dockerfile, you can build the image with
docker-compose build
Once the application has launched, you can test the application by navigating to: http://localhost:8888/ to access the dashboard.

Also, there is a TLS version running in port 443, so you can test the application by navigating to: https://localhost/ to access the dashboard.
For more information, see TLS
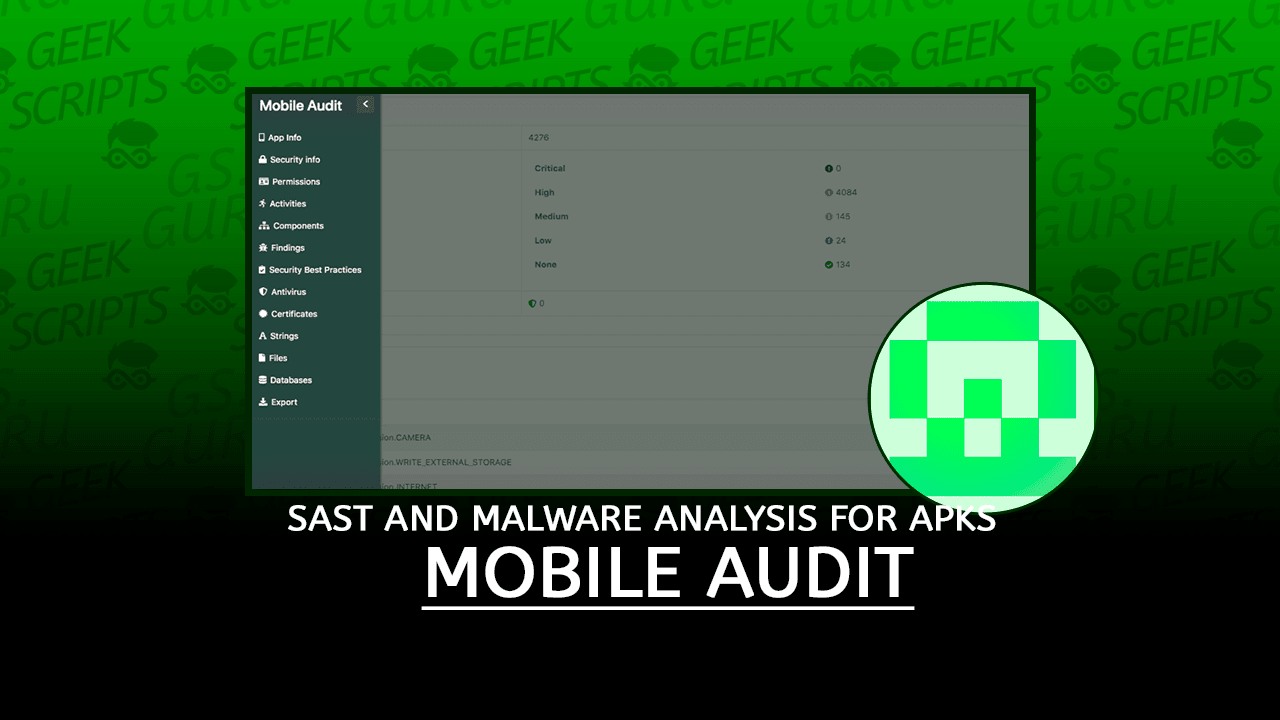
In each of the scans, it would have the following information:
- Application Info
- Security Info
- Components
- SAST Findings
- Best Practices Implemented
- Virus Total Info
- Certificate Info
- Strings
- Databases
- Files
For easy access there is a sidebar on the left page of the scan:

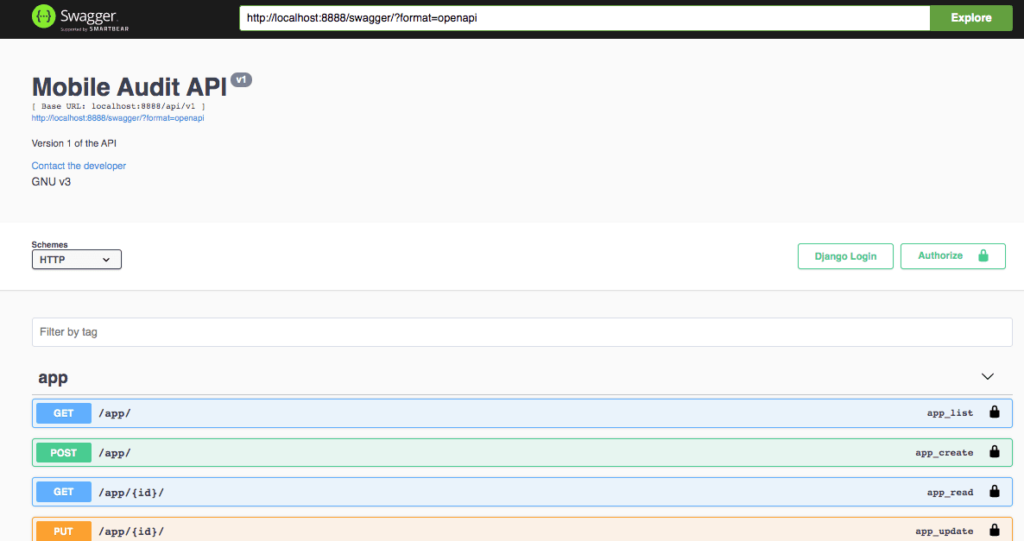
API v1
REST API integration with Swagger and ReDoc.
- Endpoint to authenticate and get token:
/api/v1/auth-token/ - Once authenticated, use header in all requests:
Authorization: Token <ApiKey>
ReDoc
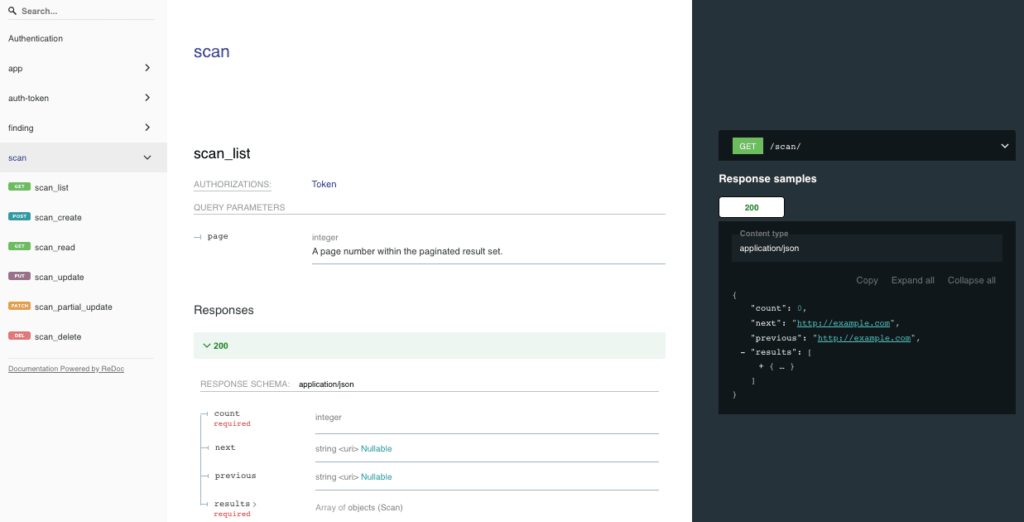
Endpoints
- A JSON view of the API specification at
/swagger.json - A YAML view of the API specification at
/swagger.yaml - A swagger-ui view of your API specification at
/swagger/ - A ReDoc view of your API specification at
/redoc/
TLS
Pre-requirements
- Add the certificates into
nginx/ssl - To generate a self-signed certificate:
openssl req -x509 -nodes -days 1 -newkey rsa:4096 -subj "/C=ES/ST=Madrid/L=Madrid/O=Example/OU=IT/CN=localhost" -keyout nginx/ssl/nginx.key -out nginx/ssl/nginx.crt
Nginx configuration
- TLS – port 443:
nginx/app_tls.conf - Standard – port 8888:
nginx/app.conf
There are two volumes in docker-compose.yml with the configurations. By default both 443 and 8888 ports will be available, but use only TLS configuration for production deployments.
- ./nginx/app.conf:/etc/nginx/conf.d/app.conf
- ./nginx/app_tls.conf:/etc/nginx/conf.d/app_tls.confEnvironment variables
All the environment variables are in a .env file, there is an .env.example with all the variables needed. Also there are collected in app/config/settings.py:
CWE_URL = env('CWE_URL', 'https://cwe.mitre.org/data/definitions/')
MALWAREDB_ENABLED = env('MALWAREDB_ENABLED', True)
MALWAREDB_URL = env('MALWAREDB_URL', 'https://www.malwaredomainlist.com/mdlcsv.php')
VIRUSTOTAL_ENABLED = env('VIRUSTOTAL_ENABLED', False)
VIRUSTOTAL_URL = env('VIRUSTOTAL_URL', 'https://www.virustotal.com/')
VIRUSTOTAL_FILE_URL = env('VIRUSTOTAL_FILE_URL', 'https://www.virustotal.com/gui/file/')
VIRUSTOTAL_API_URL_V3 = env('VIRUSTOTAL_API_URL_V3', 'https://www.virustotal.com/api/v3/')
VIRUSTOTAL_URL_V2 = env('VIRUSTOTAL_API_URL_V2', 'https://www.virustotal.com/vtapi/v2/file/')
VIRUSTOTAL_API_KEY = env('VIRUSTOTAL_API_KEY', '')
VIRUSTOTAL_UPLOAD = env('VIRUSTOTAL_UPLOAD', False)
DEFECTDOJO_ENABLED = env('DEFECTDOJO_ENABLED', False)
DEFECTDOJO_URL = env('DEFECTDOJO_URL', 'http://defectdojo:8080/finding/')
DEFECTDOJO_API_URL = env('DEFECTDOJO_API_URL', 'http://defectdojo:8080/api/v2/')
DEFECTDOJO_API_KEY = env('DEFECTDOJO_API_KEY', '')mobileAudit (this link opens in a new window) by mpast (this link opens in a new window)
Django application that performs SAST and Malware Analysis for Android Mobile APKs