This tool allows to statically analyze windows, linux, osx, executables and also APK files.
You can get:
- What DLL files are used.
- Functions and API’s.
- Sections and segments.
- URL’s, IP addresses and emails.
- Android permissions.
- File extensions and their names.
Qu1cksc0pe aims to get even more information about suspicious files and helps to user realizing what that file capable of.
- Usage:
python3 qu1cksc0pe.py --file suspicious_file --analyze - Alternative usage:
python3 qu1cksc0pe.py --file [PATH TO FILE] --analyze
Screenshot

Setup
Necessary python modules:
puremagic=> Analyzing target OS.androguard=> Analyzing APK files.prettytable=> Pretty outputs.fleep=> Analyzing target file’s magic numbers.tqdm=> Progressbar animation.colorama=> Colored outputs.oletools=> Analyzing VBA Macros.spacy=> Natural Language Processing for string analysis.
Installation of python modules: pip3 install -r requirements.txt
Gathering other dependencies:
- VirusTotal API Key:
https://virustotal.com - Binutils:
sudo apt-get install binutils - ExifTool:
sudo apt-get install exiftool - Strings:
sudo apt-get install strings
Scan arguments
Usage:
python3 qu1cksc0pe.py --file suspicious_file --analyze
Multiple analysis
Usage:
python3 qu1cksc0pe.py --multiple FILE1 FILE2 ...
Hash scan
Usage:
python3 qu1cksc0pe.py --file suspicious_file --hashscan
Multiple hash scanning
Usage:
python3 qu1cksc0pe.py --multihash FILE1 FILE2 ...
VirusTotal
Usage for –vtFile:
python3 qu1cksc0pe.py --file suspicious_file --vtFileUsage for –vtUrl:
python3 qu1cksc0pe.py --vtUrl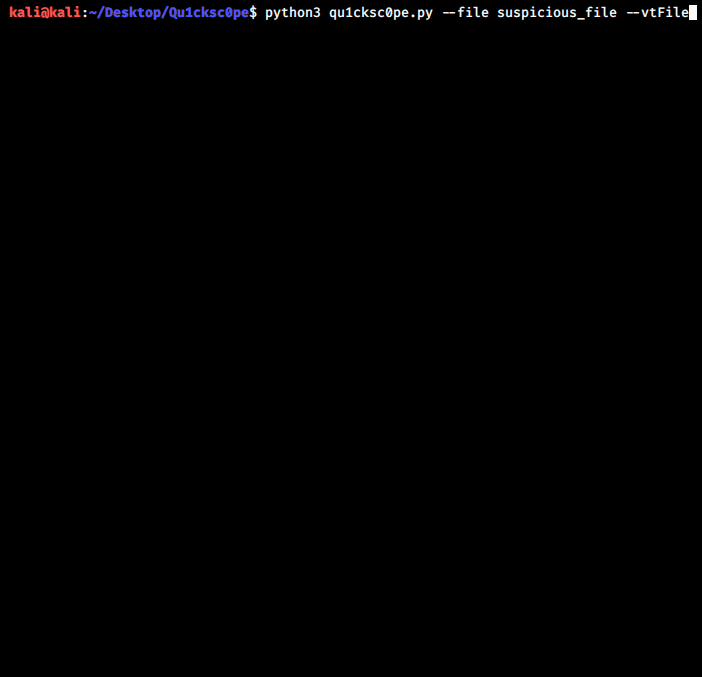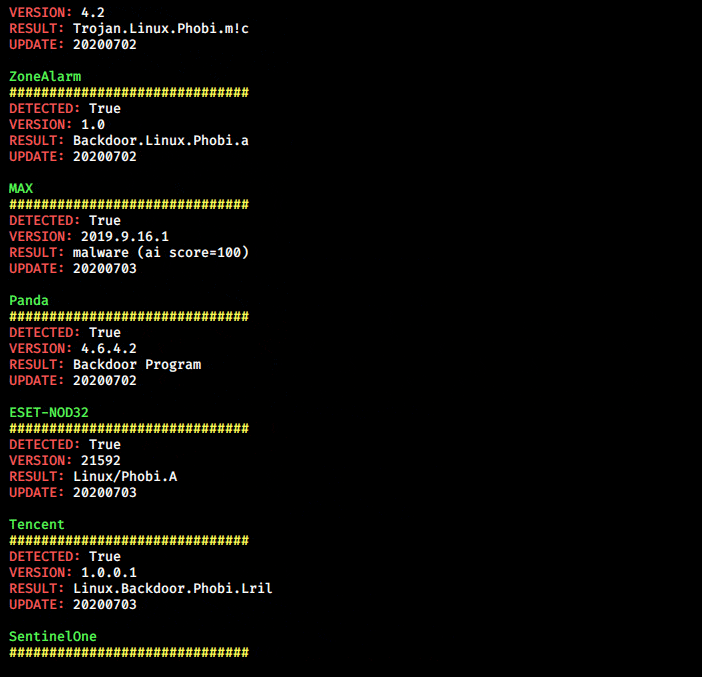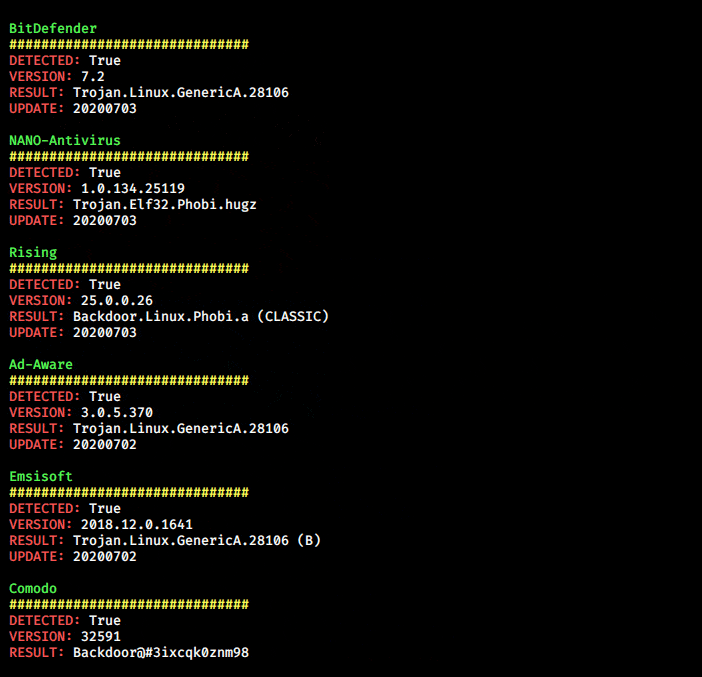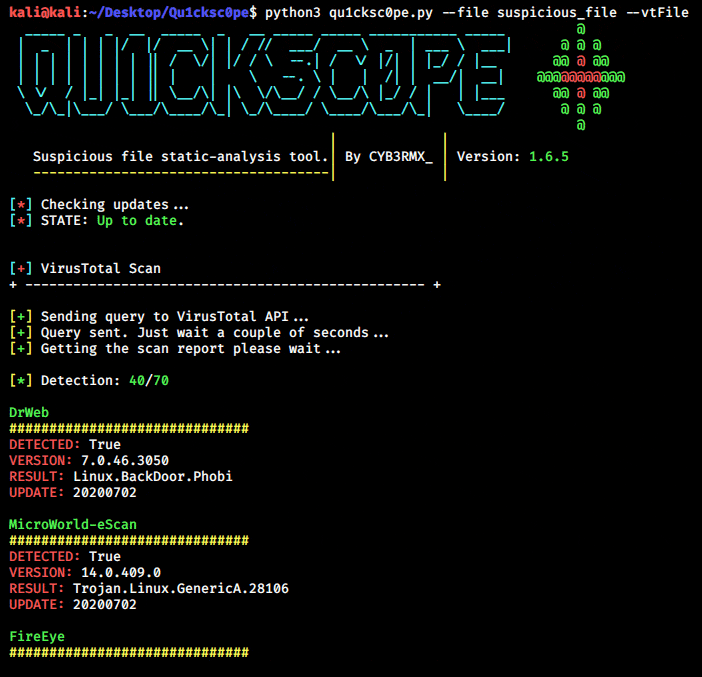
Folder scanning
Hash scan: python3 qu1cksc0pe.py --folder SUSPICIOUS_FOLDER --hashscan
Packed files: python3 qu1cksc0pe.py --folder SUSPICIOUS_FOLDER --packer
Domain
Usage: python3 qu1cksc0pe.py --file suspicious_file --domain
Informations about categories
Registry
This category contains functions and strings about:
- Creating or destroying registry keys.
- Changing registry keys and registry logs.
File
This category contains functions and strings about:
- Creating/changing/infecting/deleting files.
- Getting informations about file contents and file systems.
Networking/Web
This category contains functions and strings about:
- Communicating malicious hosts.
- Download malicious files.
- Sending informations about infected machine and its user.
Process
This category contains functions and strings about:
- Creating/infecting/terminating processes.
- Manipulating processes.
Dll/Resource Handling
This category contains functions and strings about:
- Handling DLL files and another malware’s resource files.
- Infecting and manipulating DLL files.
Evasion/Bypassing
This category contains functions and strings about:
- Manipulating Windows security policies and bypassing restrictions.
- Detecting debuggers and doing evasive tricks.
System/Persistence
This category contains functions and strings about:
- Executing system commands.
- Manipulating system files and system options to get persistence in target systems.
COMObject
This category contains functions and strings about:
- Microsoft’s Component Object Model system.
Cryptography
This category contains functions and strings about:
- Encrypting and decrypting files.
- Creating and destroying hashes.
Information Gathering
This category contains functions and strings about:
- Gathering all informations from target hosts. Like process states, network devices etc.
Keyboard/Keylogging
This category contains functions and strings about:
- Tracking infected machine’s keyboard.
- Gathering information about targets keyboard.
- Managing input methods etc.
Memory Management
This category contains functions and strings about:
- Manipulating and using target machines memory.
Qu1cksc0pe (this link opens in a new window) by CYB3RMX (this link opens in a new window)
Open source “Anti-Malware” project.

