SSH-MITM is a man in the middle SSH Server for security audits and malware analysis.
Password and publickey authentication are supported and SSH-MITM is able to detect, if a user is able to login with publickey authentication on the remote server. This allows SSH-MITM to acccept the same key as the destination server. If publickey authentication is not possible, the authentication will fall back to password-authentication.
When publickey authentication is possible, a forwarded agent is needed to login to the remote server. In cases, when no agent was forwarded, SSH-MITM can rediredt the session to a honeypot.

Features
- publickey authentication
- accept same key as destination server
- hijacking and logging of terminal sessions
- store and replace files during SCP/SFTP file transferes
- port porwarding
- audit clients against known vulnerabilities
- plugin support
Installation
SSH-MITM can be installed as a Ubuntu Snap, PIP-Package or AppImage and even runs on Android devices
# install ssh-mitm as snap package
$ sudo snap install ssh-mitm
# install ssh-mitm as python pip package
$ pip install ssh-mitm
Install as AppImage
$ wget https://github.com/ssh-mitm/ssh-mitm/releases/latest/download/ssh-mitm-x86_64.AppImage
$ chmod +x ssh-mitm*.AppImageQuickstart
To start SSH-MITM, all you have to do is run this command in your terminal of choice.
$ ssh-mitm --remote-host 192.168.0.x:PORTNow let’s try to connect. SSH-MITM is listening on port 10022.
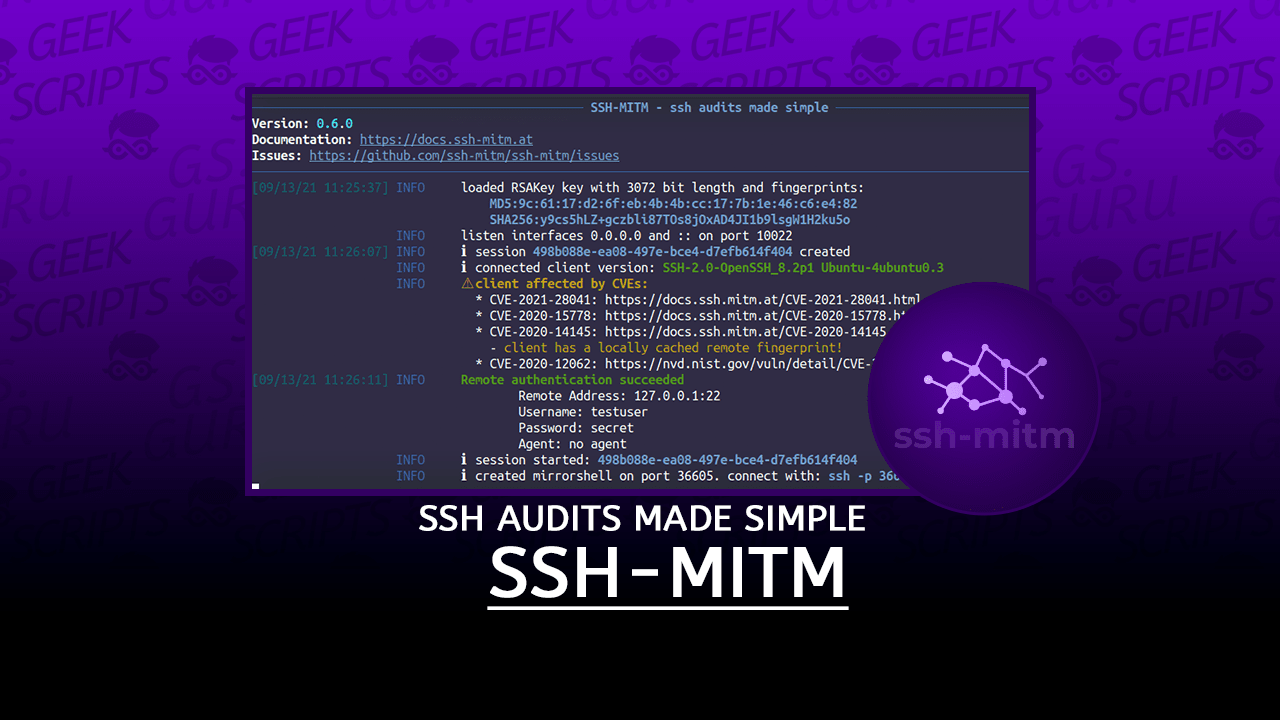
$ ssh -p 10022 testuser@proxyserverYou will see the credentials in the log output.
INFO Remote authentication succeeded
Remote Address: 127.0.0.1:22
Username: testuser
Password: secret
Agent: no agentSession hijacking
Getting the plain text credentials is only half the fun. When a client connects, the ssh-mitm starts a new server, which is used for session hijacking.
INFO ℹ created mirrorshell on port 34463. connect with: ssh -p 34463 127.0.0.1
To hijack the session, you can use your favorite ssh client.
$ ssh -p 34463 127.0.0.1Try to execute somme commands in the hijacked session or in the original session.
The output will be shown in both sessions.
Publickey authentication
SSH-MITM is able to verify, if a user is able to login with publickey authentication on the remote server. If publickey authentication is not possible, SSH-MITM falls back to password authentication. This step does not require a forwarded agent.
For a full login on the remote server agent forwarding is still required. When no agent was forwarded, SSH-MITM can redirect the connection to a honeypot.
ssh-mitm --fallback-host username:password@hostname:portssh-mitm (this link opens in a new window) by ssh-mitm (this link opens in a new window)
ssh mitm server for security audits supporting public key authentication, session hijacking and file manipulation